Phase I: Deploying the Active Directory Target
DEPLOYMENT CONFIRMED: Hack Academy's OSCP Active Directory Chain Practice Lab.
> ACTIVE VERSION: CHAIN #2 > QUEUED: CHAIN #3
System Deployment
Although this project was originally scheduled to begin in January, I felt a strong urge to dive in early. I simply couldn't wait to start deploying and pentesting Active Directory environments. I am currently deeply fascinated by the entire AD ecosystem and my goal is to learn as much as possible. After all, it remains the industry standard for enterprise identity management, making it a critical area of study.
Definition: Microsoft's proprietary directory service acting as the centralized database for network identity, authentication, and policy management.
Why is this critical for Red Teaming?
- [!] The Standard: Used by 95% of Fortune 500 companies. To hack enterprise networks, you must speak AD.
- [!] Keys to the Kingdom: AD controls "who can do what." Compromising a Domain Admin account grants total control over every server, workstation, and user in the environment.
- [!] Attack Surface: It relies on legacy protocols (Kerberos, NTLM, LDAP) which are often misconfigured. This allows for attacks like Kerberoasting, DCSync, and Pass-the-Hash.
Asset Acquired: OSCP Active Directory Chain Practice Lab
This is not a random setup. This lab is a downloadable VM pack purpose-built to replicate an OSCP-style Active Directory environment. It simulates real attack chains, forcing us to move beyond simple exploits and practice the full lifecycle:
Initial enumeration & footing.
Vertical movement to Admin.
Pivot between workstations.
Full Post-Exploitation.
"The network topology, host roles, and vulnerabilities are arranged so you practice the same steps you will encounter during exam-style AD challenges. Everything is designed for learning by doing, not just reading."
>> Objective: Use this high-fidelity simulation to build the confidence needed to crush the exam.
Goal: Construct a high-fidelity target range for adversary simulation.
- [+] Infrastructure: Deploy Domain Controller & Workstations on virtualized environment.
- [+] Red Teaming: Simulate attack scenarios and master standard AD attack vectors.
- [+] Verification: Validate domain connectivity and replication services.
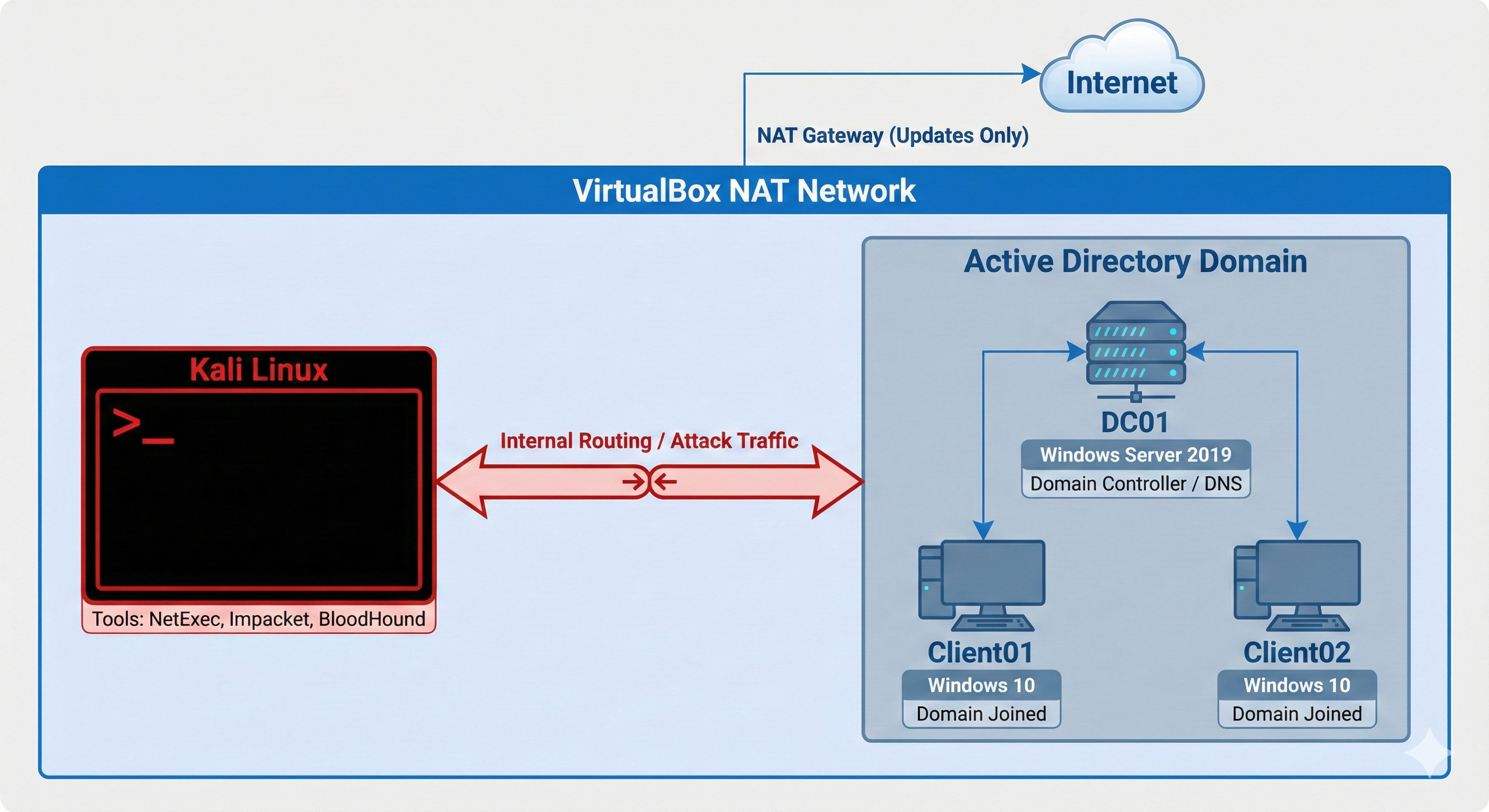
For this lab environment, I chose to import the appliances directly. The setup consists of a Windows Server acting as the Domain Controller (DC01) and two Windows 10 client workstations.
My priority was to establish a realistic but isolated network; I configured the network adapters to use an internal "NAT Network." This ensures the machines can communicate with each other and reach the internet for necessary updates, while keeping the vulnerable Active Directory services segregated from my main home network.
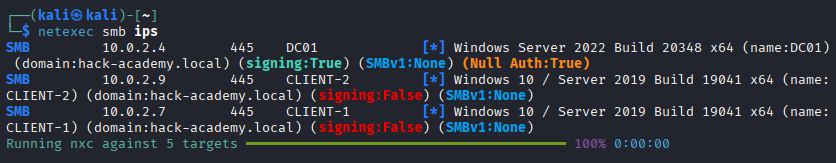
With the network configured, the next step is to verify that our Attack Box (Kali) can communicate with the target domain. I used a tool called NetExec on this part.
ComputerName : DC01
RemoteAddress : 10.0.2.4
RemotePort : 445
InterfaceAlias : Ethernet
SourceAddress : 10.0.2.5
TcpTestSucceeded : True
With connectivity established and services responding, the environment is ready for the enumeration phase.
To successfully compromise and audit the domain, we need a specific set of tooling. This lab relies on standard offensive security tools found in Kali Linux, with a focus on network enumeration and protocol abuse.
NetExec (NXC)
v1.4.0The "Smooth Operator." The modern fork of CrackMapExec. It is the swiss-army knife for enumerating AD protocols (SMB, LDAP, MSSQL, WinRM).
ENUMERATION SPRAYINGImpacket
LIBRARYA collection of Python classes for working with network protocols. Essential for executing attacks like SecretsDump, GetNPUsers, and SMBRelay.
EXPLOITATION KERBEROSBloodHound
VISUALIZATIONUses graph theory to reveal hidden relationships and attack paths within an Active Directory environment (e.g., shortest path to Domain Admin).
AUDIT MAPPINGVirtualBox
HYPERVISORHosting the infrastructure. Configured with "NAT Network" to allow internal routing between the DC and Clients while maintaining internet access.
INFRASTRUCTURE Objective: Exploit misconfigurations to gain initial domain user access.
> Enumeration | AS-REP Roasting | Password Cracking | Local Admin
Objective: Escalate privileges to Domain Admin via protocol abuse.
> Service Hijacking | Mimikatz | LSA Secrets | Persistence
Infrastructure deployed. Proceed to Enumeration & Initial Access operations.