Thesis: Command & Control Frameworks (Grade 5/5)
Mythic C2 Framework – login page
Custom C2 Infrastructure
For my Bachelor's thesis, I focused on the practical implementation of a Command and Control (C2) infrastructure to understand modern adversary tradecraft. I selected the Mythic C2 framework for its modularity and deployed it on a Kali Linux environment using Docker containers.
The project involved simulating full attack chains against both Windows and Linux targets (Parrot OS), utilizing agents like Apollo and Poseidon to execute post-exploitation tasks while maintaining operational security (OpSec).
Status: Completed (Grade: 5/5)
Focus: Red Teaming, Fileless Malware, Traffic Analysis
Official Mythic C2 documentation: Mythic C2 Docs
The Full Thesis (Finnish)
While this post summarizes the key technical findings in English, the full academic documentation regarding the infrastructure construction and penetration testing is available below.
Technical Deep Dive: Linux Evasion
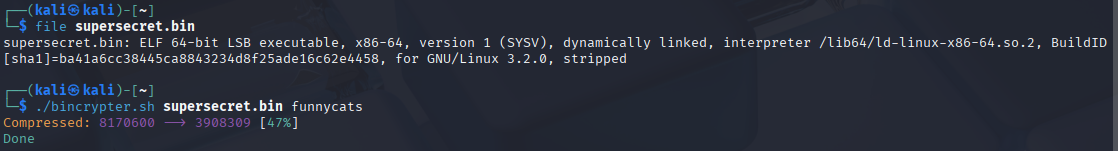
1. Payload Obfuscation (Bincrypter)
To demonstrate evasion techniques against Linux targets, I moved beyond standard payloads. I utilized Bincrypter to obfuscate the Poseidon agent (an ELF binary).
The screenshot above shows the obfuscation process. Bincrypter compresses and encrypts the original binary into a shell script. In my testing, this effectively masked the executable from static analysis tools, as the payload appeared as a high-entropy data blob rather than a known malicious file format.
2. Fileless Execution (memfd_create)
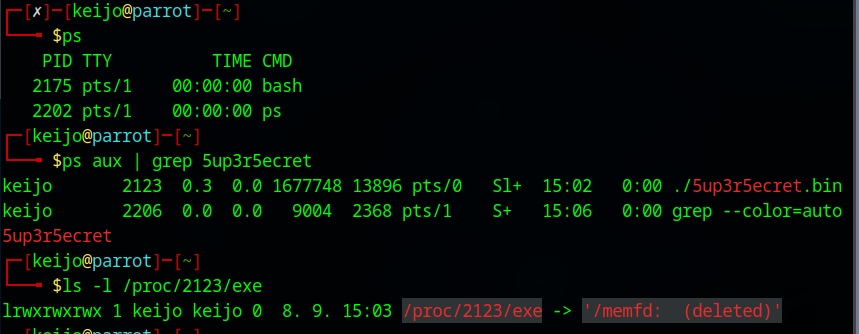
A key objective of the thesis was to achieve persistence without leaving forensic artifacts on the disk. The obfuscated payload leveraged the Linux syscall memfd_create.
The Execution Mechanics:
- Allocation: The script allocates an anonymous file descriptor in RAM.
- Decryption: The encrypted payload is decrypted directly into this memory buffer.
- Execution: The payload is executed via
execvefrom the file descriptor.
As seen in the process list (ps aux) in the image above, the agent runs successfully as /memfd: (deleted). This confirms that the binary exists only in volatile memory, bypassing standard disk-based antivirus scanning and complicating forensic recovery.
Conclusion
This project demonstrated that building a robust C2 infrastructure requires more than just server setup; it demands a deep understanding of network protocols and operating system internals. By analyzing the traffic in Wireshark, I was able to verify the effectiveness of SSL-encrypted channels (HTTPS) versus unencrypted HTTP traffic.
The thesis received the highest possible grade (5/5). It bridged the gap between theoretical knowledge and practical Red Teaming, particularly regarding the use of advanced evasion techniques like fileless execution.